Do you know how to categorize various types of data? Can you describe the differences between data loss, data leak, and data breach? And can you guess what data is the most vulnerable to security incidents? Read on and find out.
Data is an essential part of every business – and each moment, the amount of data existing worldwide increases exponentially. When customers, employees, or clients of your brand entrust you with their digital information, they also have an expectation that you will protect their privacy – and, of course, the sensitive data processed and/or held by your brand.
Data protection processes and tools can help you preserve your company’s safety, reputation, and competitive advantage by keeping both competitors and cybercriminals from stealing your know-how, innovative ideas, and even clients or employees. When the data of your company gets into the wrong hands, the situation can cost you time, money, and energy. That's why it pays to have thorough protection.
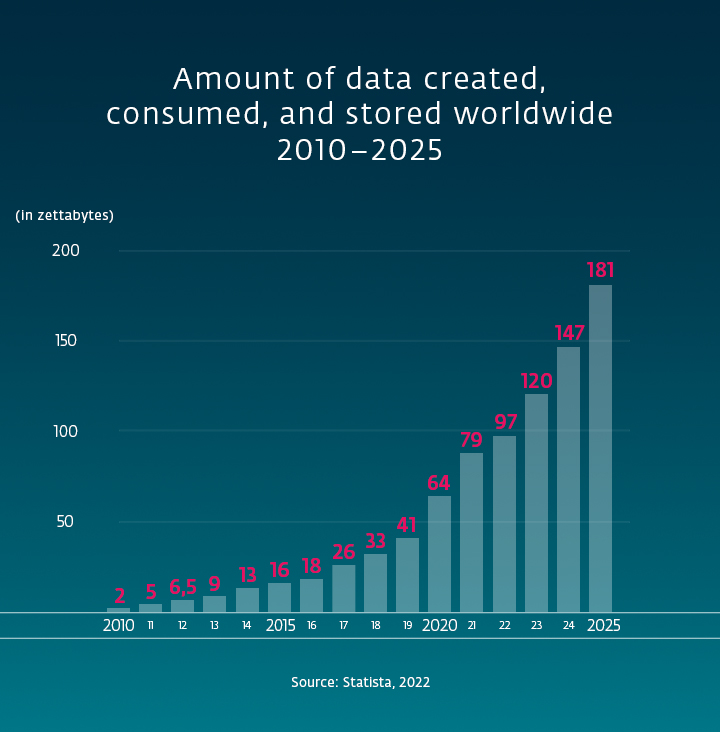
There are many types of data, and when it comes to digital security, each piece of information deserves an individual approach. So, how do you differentiate among the various categories? There are many possible criteria that can be taken into consideration, and thus, the classification systems can be different in each company. Data can be classified manually or automatically, based on its contents and context. One type of data categorization you’ll probably encounter in any business is classification based on confidentiality.
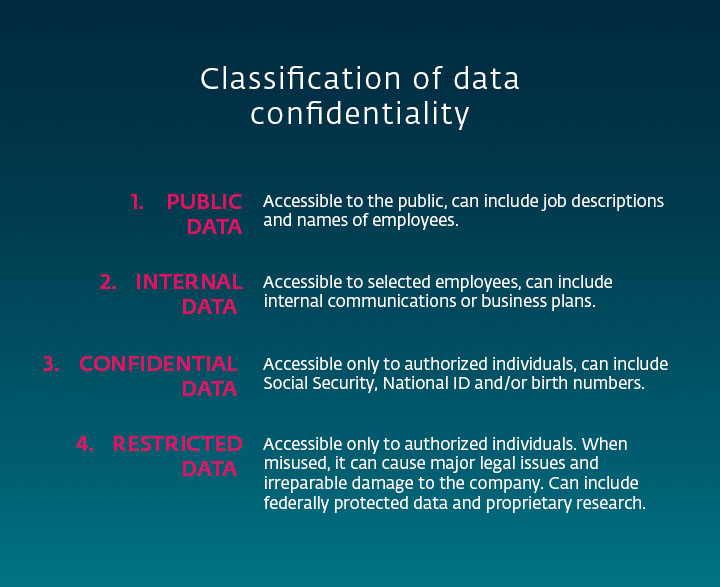
The further down the list the data above appears, the better you’ll need to protect it. The level of confidentiality depends on the content of the data, legal requirements (GDPR, for instance), etc. Besides confidentiality, your data can be classified according to its current state into three basic categories.
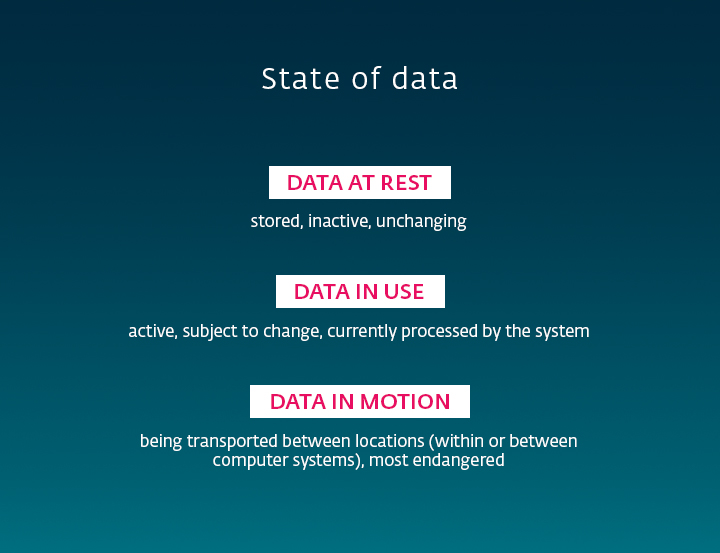
Finally, in order to keep your data secure, it helps to know what you are protecting it from. In essence, there are three basic types of problems your business can encounter.
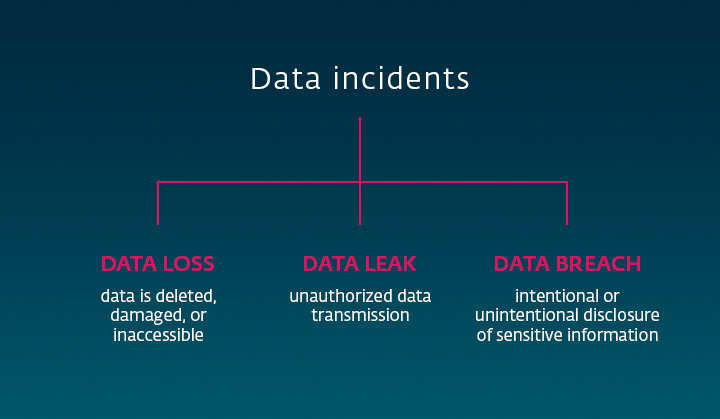
Data incidents commonly happen at endpoints, including computers, phones, printers and shared network folders. To protect your endpoints (and more), you can equip your company with a data loss protection (DLP) strategy and software that goes beyond endpoint security solutions, to protect your business from having its data leaked outside the company.
An essential part of data loss protection is implementing a backup and recovery software. Read more about its usefulness and learn how to select the right solution for your company.