As an IT manager, you play a key role in protecting your organisation from social engineering threats. The challenge is not only to protect the company's systems and data, but also to ensure that your employees remain informed and vigilant against these tactics.
If someone in your company received a suspicious email from an unknown sender asking them to quickly click on a link, would they do it? Thanks to the various cybersecurity training sessions that have become a regular part of many organisations today, there is a good chance that they would see through this malicious attempt. But what if it came from an email address within the company, urgently requesting access to some internal documents? The familiarity of the sender's name and the seemingly official nature of the request can easily gain one’s trust. And that is exactly what social engineering attacks like phishing take advantage of.
Pretexting is a more elaborate and patient approach when compared to traditional phishing. It is based on a fabricated but believable pretext or story to trick the victim into divulging information or to perform specific actions. This might include posing as a trusted colleague, service provider, or authority figure to gain the victim's trust and extract information. Oftentimes, the attacker builds a rapport with their target, and engages in extended conversations or multiple interactions to gradually extract the desired information without raising any suspicion.
|
Casino cyber heist In September 2023, the glamour of Las Vegas was dimmed by a different kind of spectacle – social engineering attacks on renowned casinos like MGM Resorts and Caesars Entertainment. Customer data, including driver's license and social security numbers, were stolen during a wide-scope social engineering attack. How did it all unfold? It appears that the culprits – the ALPHV and the Scattered Spider hacking groups – set their sights on identity management company Okta. Ultimately, they managed to breach the defences of Okta’s five unsuspecting clients, including MGM and Caesars. What's particularly intriguing is the second group's tactic. The Scattered Spider is known to contact an organisation's information security teams by phone, pretending to be an employee needing their password reset. "They tend to have most of the information they need before that call to the helpdesk – that is the last step," revealed Marc Bleicher, a security analyst. It's highly likely that a similar social engineering technique was also used to get the data of Las Vegas casino giants: in past months, Okta reported a recurring pattern where hackers posed as employees of targeted firms, smoothly manipulating IT helpdesks into providing duplicate access. These incidents prove that pretexting is a substantial threat –not only IT specialists but all employees should be aware of. |
For the purposes of keeping pace with rapid developments in the field of cybercrime, it is helpful to distinguish between phishing and pretexting. According to the 2023 Verizon Data Breach report, around half of all social engineering attacks are pretexting incidents, a rate that has doubled since the previous year.
Action varieties in social engineering incidents according to Verizon Data Breach Report 2023
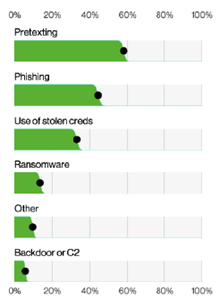
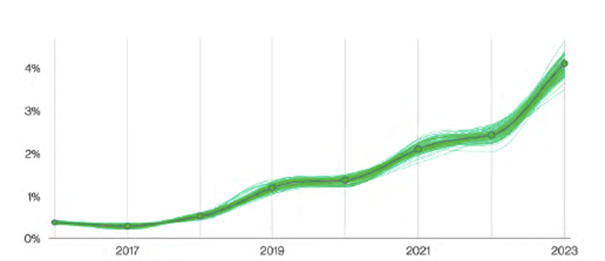
While email still accounts for most social engineering attacks, they can also occur via social media and other communication channels. Unsurprisingly, the use of pretexting makes social engineering attacks even more successful – and, therefore increasingly more common. The median amount stolen in these attacks has also increased in recent years, reaching £42,000 in 2022.
Pretexting incidents over time, according to Verizon Data Breach Report 2023
How does pretexting work?
This online scam relies on a fabricated story to access valuable information or assets. And what every good story needs are believable characters and an engaging plot.
The character is the role the scammer plays in this fake story. The perpetrator typically impersonates someone with credibility and authority, such as the victim’s boss, a governmental institution, or a service provider. It is no exception that they even try to disguise as someone you know personally.
The plot is what gives this fabricated story the reasoning. The staged situations may be generic – e.g., a request for changing your password – or more specific, such as demanding to change the invoicing details of a vendor in corporate systems.
To make pretexting believable, attackers often use information gathered online about their targets' interests, professional details, or even personal relationships. According to a report from Omdia, approximately 100 minutes of simple Googling can provide hackers with enough information from public sources (mainly social media) to create a convincing story.
Next level: Business email compromise (BEC)
What makes the characters more believable and, therefore, the technique of pretexting even more dangerous, is the use of a seemingly legitimate email address or phone number the victim is familiar with. This is called business email compromise (BEC), a type of attack that relies on the ability to disguise as someone within the company or a trusted external partner. It comes in a variety of forms:
- Look-alike domains can have just a minor deviation in spelling from a legitimate email address, such as “conpany” instead of “company”, or “Ana” instead of “Anna”.
- Domain spoofing is a technique of faking the display name or email address by manipulating the email protocol (SMTP). SMTP can also allow the sender to define a different address when you hit reply, ensuring that they receive the responses.
- The attacker can also use an actual email or social media account that has been compromised, usually because of leaked credentials.
The most common goal of a BEC attack is to convince the target to send money to the attacker while believing that they are performing a legitimate, authorised business transaction. According to IBM, the average data breach cost from a BEC attack climbs to £4 million. This staggering number emphasises the importance of understanding and combating these threats effectively.
Defending your company against pretexting and BEC attacks
While the tactics used in pretexting and BEC attacks are complex, the principles of defence remain the same as for any form of social engineering attack. Here is what your employees should know:
Caution and vigilance
Be cautious of unsolicited requests, especially those that demand urgency. Pause and evaluate the situation before proceeding.
Verification before action
Always verify the authenticity of requests, even if they appear to come from trusted sources. Use known contact information to confirm any unusual or sensitive demands.
Choosing established channels
In a corporate environment, communicate only through pre-approved communication channels.
Spotting inconsistencies
Be vigilant about inconsistencies in emails, such as unusual language, misspellings, or changes in writing style.
And here is what you, as a person responsible for cybersecurity within your company, can do:
Continuous education
Stay informed about evolving threats and attack techniques, and try to build strong cyber awareness in your company. Regular training can empower your team to recognise and respond to suspicious activities.
Safeguarding sensitive data
Protect your personal and organisational data through a strong password policy, multifactor authentication, encryption, and secure storage practices.
Preparation and response
Recognise that even with the best prevention measures, some attacks may succeed, so have a response plan in place to minimise damage and swiftly mitigate the effects in case of a successful attack.
Pretexting and BEC attacks stand as examples of the constant progress cybercriminals are – unfortunately – making. While there is no fool proof shield against cyber threats, arming yourself with awareness can go a long way. Remember, being secure is a journey. It's about minimising risks, responding effectively when something slips through the cracks, and continually adapting to the ever-changing landscape of digital security.




