When we try to protect our data from cybercriminals, there is one shield we should all use: passwords. Safeguarding private data, banking details, sensitive files, and more, passwords are a key that criminals desire to obtain – and brute force attacks are one way to reach this goal. Get to know the various types of this threat and find out how to lower the chance of becoming a victim.
Maintaining proper password hygiene can be an uneasy task in the digital age we live in.

For cybercriminals, login credentials are a lucrative commodity – and companies are well aware of that. To protect your privacy, you should continuously strive to make security restrictions more complex, for instance, by requiring increasingly more complex passwords from your employees.
Still, some employees underestimate cybercriminals, believing that unless they use insecurely short and simple passwords (such as “password123”), they are safe from threats, including brute force attacks.
Nothing could be further from the truth. During brute force attacks, cybercriminals attempt to guess or obtain user credentials and gain access to their victims’ accounts – and, as shown by the statistics, surprisingly complex passwords are often used in these incidents.
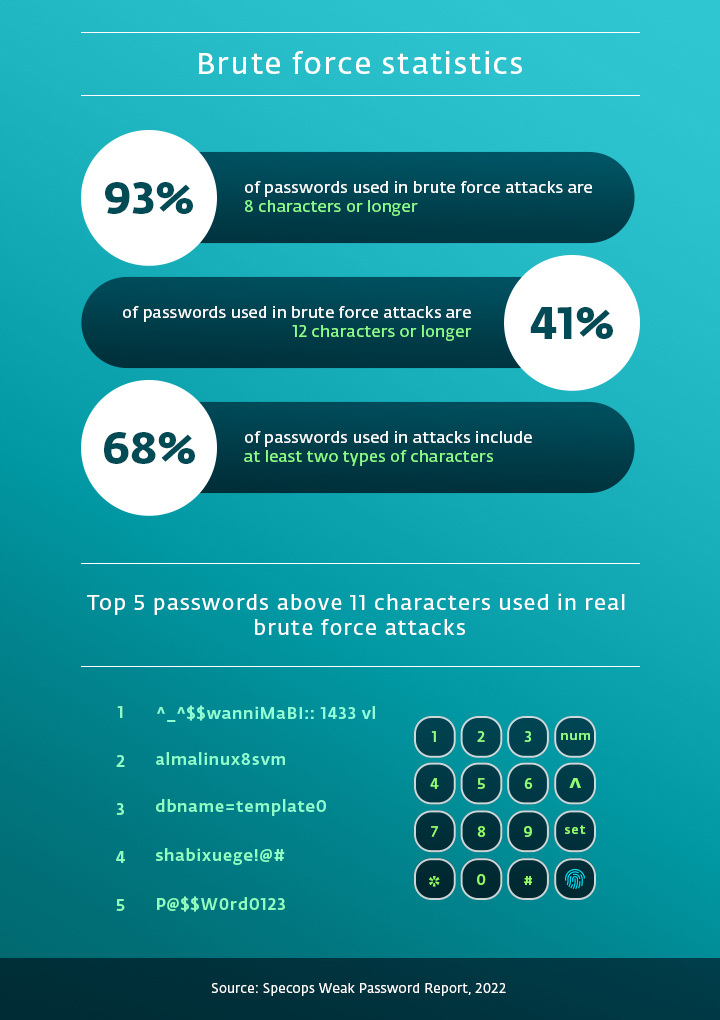
As the numbers suggest, hackers are aware of the developments in password security and readily adapt their tactics to achieve success. The threat of brute force attacks can come in many forms – let’s get to know them better.
1. Simple brute force attack
In a simple brute-force attack, hackers try to guess the password without using any specialised software or database. They may, for instance, test the most common password combinations or use the information accessible online, for example, on the victim’s social media.
2. Password spraying
During password spraying attacks, hackers use a list of the most frequent passwords and passphrases, and by employing a special spraying software or a toolkit, they test (“spray”) one password on many different accounts. As a result, lockout policies may fail to notice the attack, and additionally, one attack may lead to the hackers gaining access to tens or even hundreds of different accounts.
3. Dictionary attack
Hackers try out different combinations and variations of commonly used words during a dictionary attack. The attacks are usually not executed manually – hackers often use a program that works with extensive common password lists and dictionaries (as the name of the attack insinuates) and enters the many possible password combinations into the selected system.
4. Credential stuffing
If an attacker owns a list of leaked or compromised credentials, they may use special software to enter (“stuff”) the username and password combinations into many websites. In case the affected user recycled their login data for multiple different sites – which is, unfortunately, still a common mistake – the criminals may gain access to several accounts with just one combination of credentials.
5. Reverse brute force attack
Sometimes, cybercriminals already have the password – all they need to do is to find the right user. Using the lists of passwords leaked in previous data breaches, the hackers may search different platforms and databases, trying the compromised credentials on various accounts.
6. Hybrid brute force attack
Hybrid brute force attacks combine the attack techniques described above. Commonly, hackers opt for a dictionary attack in combination with a simple brute force attack. In an attempt at breaking into different accounts – usually already knowing the usernames – they use common words and phrases in combination with a set of letters or numbers, which may be random or based on previous research on the victims.

How to shield yourself from brute force attacks
For the employees themselves, the primary measure they should adhere to is to maintain proper password hygiene. This may consist of using a unique password for each account, opting for longer passphrases containing various characters, and using a trustworthy password manager to store their credentials. Using multi-factor authentication (MFA) is also a must. Thanks to MFA, guessing your password will not immediately enable hackers to access your data.
Your company can also consider limiting invalid logins and using CAPTCHAs to prevent brute force attack tools from entering their systems. It is also advised to change passphrases periodically. Finally, you should set up a secure password policy and further enhance the safety of your employees and business by actively monitoring the activity taking place on your platforms. Following safe practices and staying alert prevents cybercriminals from surprising you.


