Your employees have probably already received emails seemingly coming from a bank or other popular online service, requesting that they “confirm” their account credentials or credit card number. This is a common phishing technique. Unfortunately, during the COVID-19 pandemic, we’ve seen once again that phishing lures are constantly changing – and they’re sometimes hard to recognise.
Phishing is a form of social engineering attack in which the attacker tries to gain access to login credentials, to get confidential information or to deliver malware. If you work in a small company, you too should be aware that the scammers behind phishing attacks would like to break into your business accounts; because phishing campaigns can target large numbers of anonymous users, not only specific victims or specific companies.

Scammers know that there’s a good chance that any message will be scanned for malicious content by the security software of your mail provider. Gmail, for example, is very good at diverting such things to a junk folder.
Since the coronavirus pandemic started to unfold, fraudsters have wasted no time in trying to profit from the uncertainty, fear and supply shortages connected to the crisis. In March 2020, there was a flood of COVID-19 themed spam, spreading malware, phishing for sensitive information or offering bogus products, as revealed in the Q1-2020 ESET Threat Report. According to Google, scammers were sending 18 million phishing emails about COVID-19 to Gmail users every day in March. In April, the BBC wrote that the tech company was blocking more than 100 million phishing emails a day, of which almost a fifth were scam emails related to the coronavirus.
Then organisers of one of Europe’s most popular security event, IFSEC, stated that online scams using the pandemic as cover appeared most frequently in the UK and USA, but penetrated almost all countries fighting the coronavirus. For instance, when citizens in Italy started to apply for coronavirus benefits, some hackers attacked Italy’s social security website, forcing it to shut down for a day.
It is no surprise that the coronavirus crisis has become one of the top lures for attackers. The appearance of any crisis brings new circumstances that provide an ideal environment for cybercriminals to innovate. At the same time, phishing attacks also benefit from the massive wave of new remote workers.
So how do you recognise suspicious emails? Here's what to watch out for:
1) Look at the sender email address
If you are not familiar with the address, be careful with the body of the message. Scammers’ email addresses used to be easier to identify. They were anonymous or had very generic names with many numbers. Sometimes the sender’s email address didn’t match the sender’s name or the content of the message. Now it can be trickier. Receiving emails from financial institutions with whom you have no relationship is obviously suspicious. But if you get an email claiming to be from your bank, closely review the email address. In some cases, the email address is the only sign of a scam, due to convincing design and email content.
2) Expect the worst from attached files or unfamiliar links
They might contain malware or send you to a malicious web destination. If you are at all suspicious, don’t open them. Competent service providers don’t send messages requiring you to log in via an embedded link. Also pay special attention to attached files – once they are opened, these attachments can give someone else complete control over your computer, initiate attacks on other computers, or send spam to any contact in your address book.
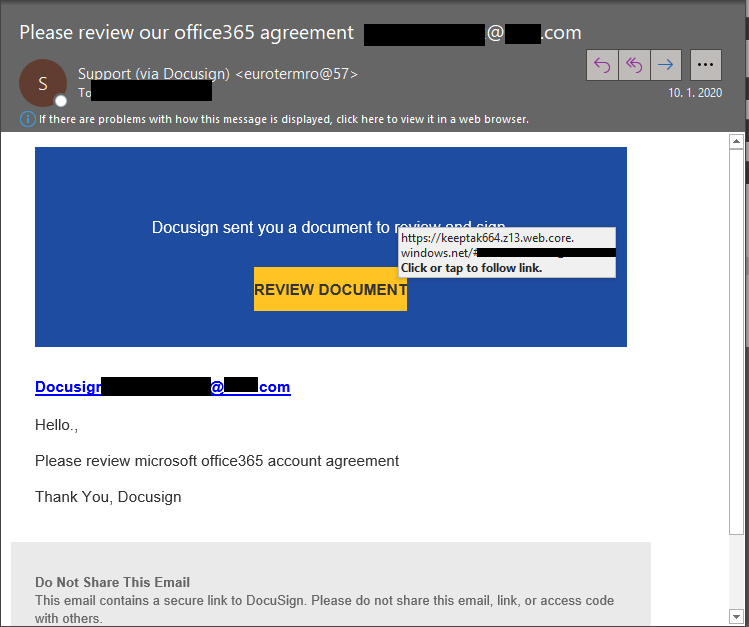
3) Note if the email is written with grammatical mistakes
Yes, poor grammar is a sign of phishing. Always be suspicious, even if you are not a language teacher. Looking for unusual language and vocabulary, or misspelled words can help prevent your organisation from becoming the next victim of cybercriminals. Keep in mind that bad spelling and other grammar mistakes are more common with phishing emails that have been translated from other languages. This kind of attack has become far rarer today, but the basic form of attack hasn’t changed much – only the quality of the social engineering and the far more professional presentation. Another linguistic element that can signal an attempted attack is generic greetings and formulations. So if an email starts "Dear recipient" or " Dear user", be wary.
4) Suspicious urgency?
The scammer wants you to panic. Don’t let threats get to you. Does the email desperately call for help, seek urgent rescue, threaten blackmail or appeal to your emotions? Beware, these are often the tactics of a cybercriminal. Do not answer an email if it uses phrasing such as: "If you do not respond within 48 hours, your account will be cancelled" or "If you don't answer, your account will be automatically deactivated."
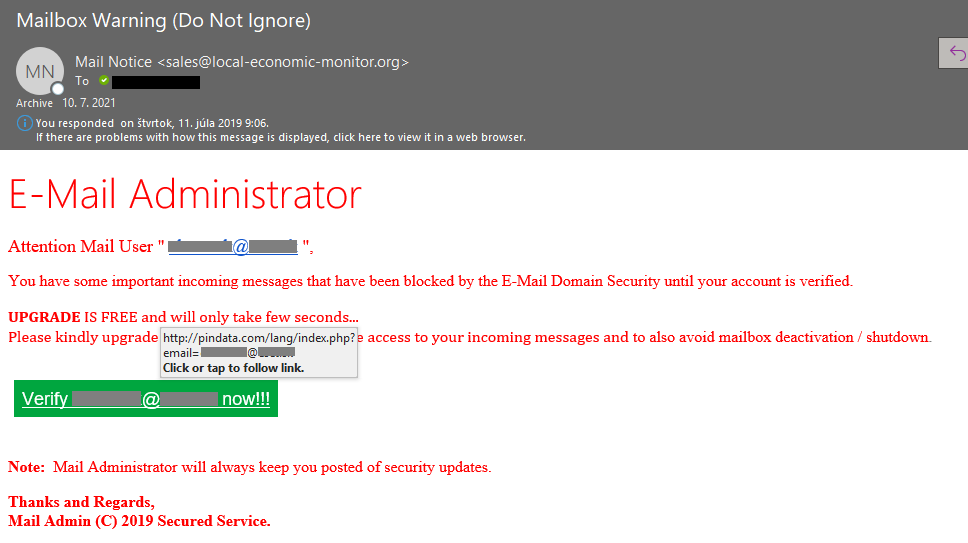
5) Too scary or too good to be true?
Remember that social engineering focusses on human weaknesses. Does the email promise you money? Does it suggest you inherited a fortune? Look for the same message in Google’s search engine. You'll probably find that thousands of other people have received the same fraudulent message. But you also have to know that cybercriminals using social engineering methods are trying to keep up with trends, for example shopping platforms. Black Friday sales can be a great opportunity for them to send out mass emails claiming issues with order and asking for your personal information.
6) The subject differs from the message
That should warn you immediately. The subject line is apples, but the message only mentions oranges? The subject of a phishing email often has nothing to do with the message. Or it mentions services you never applied for.
Homoglyph attacks arrive on the scene and you need protective technologies to detect them.
Homoglyph attacks rely on replacing characters in addresses with ones that look similar – or are even visually indistinguishable – but belong to different alphabets. These attacks are extremely dangerous for users because there is a very limited chance of detecting the trap. Like the attack on PayPal users in which the address contained the “correct letters” taken from the Latin alphabet – with two exceptions. The attackers replaced both instances of the letter P with a “P” look-alike letter, but from a different alphabet. This “P” look-alike letter was taken from the Russian alphabet, where it is equivalent to the letter R. With this kind of attack, you are dependent on protective technologies.





