High processor activity, unusual energy consumption, reduced productivity of your infrastructure. These are some of the signs that your company devices might have been misused for cryptomining. How can you prevent cryptominers from getting into your network? And why should you even care?
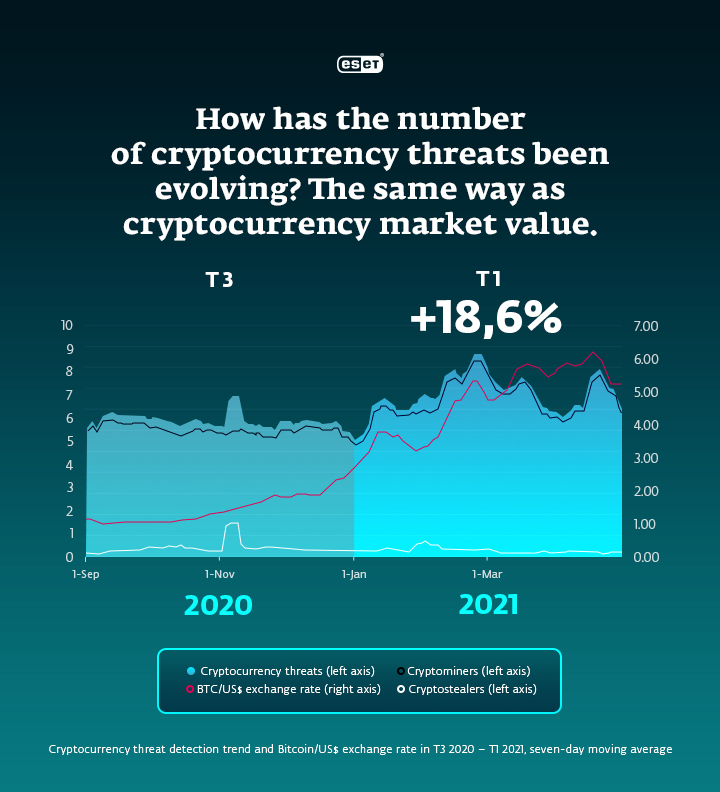
As cryptocurrencies become more popular and valuable, driven (amongst other factors) by the growing mainstream acceptance of such payment methods, they also gain the attention of attackers. No wonder that between January and April 2021, the number of cryptocurrency threats raised by almost 19%, reveals the recent ESET Threat Report. In the same period there was also a massive increase in prices of cryptocurrencies, so we can observe the correlation between rising prices of cryptocurrencies and cryptominers usage. There are multiple reasons why cryptocurrencies become an attractive target for cybercriminals, who often carry out their illegal activities via company devices, including those used by small businesses. Here's what to look for, how it happens and tips to keep your SMB safe from illicit cryptomining.
Easy come, easy get
Cryptomining has become the go-to low risk tactic for cybercriminals to gain money. They misuse electronic devices to mine cryptocurrency, installing malicious code that secretly steals the processing power. Company devices are even more tempting than private ones – since their performance is usually higher, cybercriminals also manage to mine more currency in a shorter timeframe.
As the program generally runs in the background, it is quite difficult to spot when a device has been hijacked. Still, some signs shouldn’t be ignored. When infected with cryptomining malware, the device is usually slower and the productivity and performance of the infrastructure decreases. Another warning sign is unusual energy consumption, as well as suspicious network traffic. If your Android device has been infected with cryptomining malware, you may be able to spot additional computational load causes, like a shorter battery life and noticeably increased device temperature.
The underestimated risk for SMBs
Is this an issue relevant to my small business, you might ask? Seemingly, cryptomining attacks are not as severe as other cyber threats. Nevertheless, they too have the potential to paralyse your business. "Mining usually hijacks a large portion of hardware’s processing power, reducing performance and productivity. The power-intensive process causes additional stress to the hardware components and can damage targeted devices, shortening their lifespans,” explains ESET Security Awareness Specialist, Ondrej Kubovič. Cryptomining malware can also lead to even more significant disruptions, since it exposes vulnerabilities in company infrastructure and cybersecurity posture, which can be misused by other – sometimes even advanced and sophisticated – malicious actors or their code.

Picky cryptominers
How do cryptominers infect the device at all? There are several malware types and possible strategies. The malicious program is either downloaded and installed on the device, or integrated into a web page. In the latter case, cyber criminals embed a harmful JavaScript into a webpage (or some part of it), which had been specially designed to mine cryptocurrency. This technique is called cryptojacking, and it targets mainly torrent, free streaming or pornographic websites, where internet users tend to spend more time and thus allow the miner to mine more. The most popular cryptocurrency that the attackers usually crave is Monero. “It has a higher level of transaction anonymity and, most importantly, mining with regular CPUs and GPUs is favoured while expensive and specialised hardware such as ASIC miners are deterred,” says Kubovič.
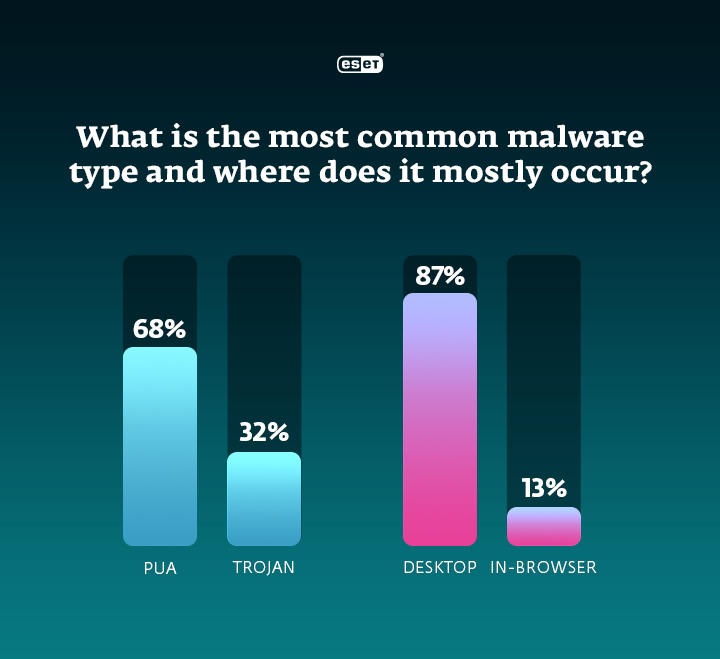
Interestingly, the majority of detected cryptominers are not the obviously malicious trojans, but potentially unwanted applications (PUAs), meaning software that might perform activities not approved or expected by the user. This category includes adware, trackware, cryptominers and more. Such a program could be installed by mistake or due to a lack of knowledge, which is why it is advised to limit administrative privileges in your company in order to mitigate the human risk factor involved.
Fewer chances for miners
Fortunately, there are ways to prevent cryptominers from infecting your devices.
1. Protect your devices with multilayered and reliable security solutions.
They help you detect cryptomining malware.
2. Implement intrusion detection software (IDS).
This allows you to identify suspicious network patterns and increase network visibility using a remote management console.
3. Follow the principle of least privilege.
User accounts should be provided with as few permissions as possible. This lowers the risk that cryptominers will spread to other devices within the same company network.
4. Use application controls that narrow the software allowed to run to a minimum.
Again, this prevents cryptomining malware from being installed on company devices.
5. Implement a good update and patching policy.
Thanks to this measure, you lower the risk that your company will be compromised via previously known vulnerabilities.
6. Monitor company systems.
Look for excessive power usage or energy consumption.
7. Filter websites that shouldn't be visited from company devices.
Create a blocklist of websites that are not necessary nor suitable for work (eg. torrents or free streaming services).
Last but not least, employee training matters – sometimes the human factor is the most vulnerable point, but by raising awareness, you can turn your comployees into your company's defence wall. Here’s how to proceed if you want to build a cyber-aware company culture.




