Voice clones created with artificial intelligence can make it all too easy for cyber attackers to get to you. Jake Moore, Global Security Advisor at ESET, has experienced this firsthand.
Voice clones created with artificial intelligence can make it all too easy for cyber attackers to get to you. Jake Moore, Global Security Advisor at ESET, has experienced this firsthand.
“The quality of the cloned voice, which was created by one of my colleagues, surprised me so much that I decided to use the same software for ‘dubious’ purposes and test how far I could go and if I could scam a small business—of course with permission,” says Jake Moore from the UK branch of ESET.
Spoiler alert: The execution was surprisingly easy and took almost no time.
Ever since the concept of artificial intelligence became popular thanks to films like Blade Runner and The Terminator, people have been curious about the potential of what this technology could create next.
However, only now, owing to more powerful computer technology and media attention, are we witnessing AI reaching a global audience, and thanks to it, we will likely start seeing creative and quite sophisticated attacks with very harmful consequences.
Using a voice clone to request money
Jake Moore spent many years working for the police, which taught him to think like a criminal. This approach has several tangible and underrated advantages: the more one thinks or even acts like a criminal (without becoming one), the better one can protect oneself. This is essential to keep up with the latest threats and anticipate future trends.
To test some of the possibilities of current artificial intelligence, Jake had to immerse himself once again in the mindset of a digital criminal and ethically attack a company.
First, he asked his acquaintance—let’s call him Harry—if he could clone his voice and use it to attack his company. Harry agreed and permitted Jake to start the experiment by creating a clone of his voice using readily available software. Obtaining Harry’s voice was quite easy—he often creates short promotional videos for his business on his YouTube channel. So, Jake just needed to combine a few of these videos, and he had a good audio sample to work with. Within minutes, he generated a clone of Harry’s voice that sounded exactly like him and could then type anything to be read out in his voice.
To make the attack more convincing, Jake decided to also hijack Harry’s WhatsApp account—with permission, of course. By swapping SIM cards, Jake gained access to the account from which he then sent a voice message to the company’s financial director—let’s call her Sally. The message contained a request for a payment of £250 to a “new supplier.” Jake chose to carry out the attack while Harry was out on a business lunch, which provided the perfect timing.
In the fake voice message, Harry stated where he was and mentioned that he needed to pay a “new architect,” promising to send the bank details separately in the next message. Additional information sent after the WhatsApp voice message was enough to convince Sally that the request was genuine. Within 16 minutes of the first message, £250 had been transferred to Jake’s personal account.
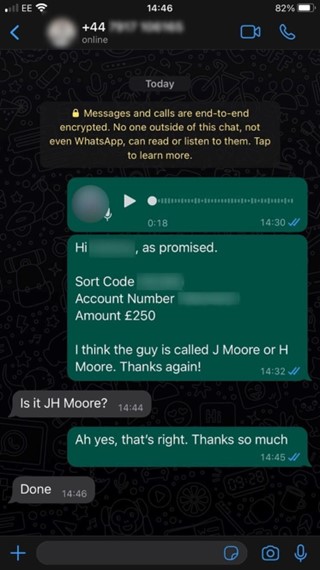
Jake admits that he was shocked by how simple it was and how quickly he convinced Sally that Harry’s cloned voice was real.
This level of manipulation worked due to a combination of related factors:
- The phone number used was the director’s
- The fabricated story matched the events of the day
- The voice message, of course, sounded like the boss
Sally later stated that all of the above was more than enough for her to comply with the request. Needless to say, the company has since added additional security measures to protect its finances. And, of course, Jake returned the £250.
Fake business WhatsApp account
Stealing someone else’s WhatsApp account through a SIM swap attack can be a somewhat lengthy method to make an attack more credible, but it happens more often than you might think. However, cybercriminals don’t necessarily have to go that far to achieve the same result.
Jake also became the target of an attack that initially seemed credible. Someone sent him a WhatsApp message posing as a friend who is a senior executive in an IT company.
The interesting dynamic of the attack was that, although Jake is used to verifying information, this message came with a linked contact name instead of appearing as a number. This was particularly intriguing because the number it came from was not saved in Jake’s contact list, and he assumed it would still display as a mobile number, not as a name.
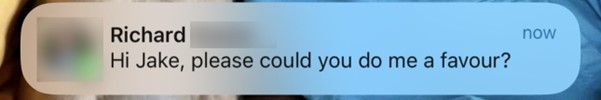
Apparently, attackers were able to do this simply by creating a WhatsApp Business account, which allows adding any name, photo, and email address to the account to make it look genuine right away. Add to that voice cloning using artificial intelligence, and voilà, we have entered the next generation of social engineering.
Fortunately, Jake knew from the start that it was a scam, but many people could fall for this simple trick, which could ultimately lead to financial loss.
As machine learning and artificial intelligence advance by leaps and bounds and become increasingly accessible to the masses, we are entering an era where technology is starting to help criminals more effectively than ever before, thanks to the refinement of all existing tools that help conceal the identity and whereabouts of criminals.
How to stay safe from voice cloning scams
Let’s go back to our experiments and walk through several basic precautions that company owners should adopt in order not to fall victim to voice cloning or other scams.
- Follow business and approving processes
- Verify individuals and processes; for example, verify all payment requests with the person who (allegedly) submits the request, even twice if necessary, and have transfers approved by two employees within your company
- Follow the latest trends in the technology world and adjust the education of your employees and safety features accordingly.
- Set up ad hoc information training for your employees.
- Use multilayered security software.
Here are several tips on how to stay safe from SIM card swaps and other attacks targeted at separating you from your personal information or money:
- Limit the amount of your personal information shared online. If at all possible, avoid publishing your address or phone number.
- Limit the number of people who can see your posts and other content on social media.
- Beware of phishing scams and other attempts to draw your personal information from you.
- Use two-factor authentication (2FA), such as authenticating app or hardware authentication device.
The importance of the 2FA cannot be stressed enough—don’t forget to also use it on your WhatsApp account and all other accounts that offer it.
Looking at the voice cloning attacks, one might get scared, but the truth is that even these advanced scams can be dodged. Following the aforementioned tips and staying vigilant can help you recognise the real voice of a person you know from some deceptive robot.




