In recent years, the risk of getting attacked by cybercriminals has been steadily increasing, and as a consequence, cyber insurance represents a progressively more popular measure to mitigate the financial impact of potential cyberattacks. Still, when trying to protect your company, cyber insurance needs to be accompanied by additional security measures. Focusing on your cyber resilience pays off.
In the first half of 2021, cyber intrusion activity globally jumped by 125 percent in comparison to the previous year. The number of ransomware attacks is rising and the development of “ransomware as a service” (RaaS) has transformed the scene of cybercrime, offering ready-to-use ransomware even to attackers of limited technical knowledge. Rapid development of the digital economy and global shift to teleworking, both happening partially as a result of the pandemic, have also caused cybercrime to rise globally.
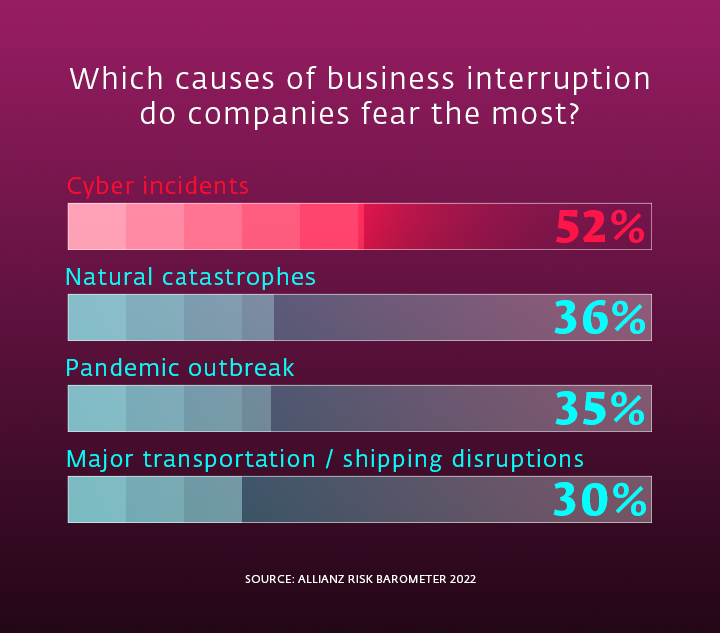
|
"Cyber insurance claims have increased significantly over the past three years, driven by the rise of losses from external manipulation of systems, as well as the increased uptake in cyber insurance. Overall, cyber-related claims seen by Allianz Global Corporate & Specialty (AGCS) increased from almost 500 in 2018 to more than 1,100 in 2020. Ransomware-related claims increased 50% year‑on‑year in 2020 (to 90), while the total number of ransomware claims received in the first half of 2021 was the same as reported during the whole of 2019 (60), according to AGCS analysis, as criminals have become more organized and better resourced.
Source: Allianz Risk Barometer 2022 |
The increased risk of danger has motivated companies to search for a safety net – a cyber insurance that would minimize the effects of impending cyberattacks. And insurance companies speedily react to such demands. Many companies believe that cyber insurance should provide them not only with the capital needed to cover the costs of the potential breach, but also to secure the help of selected specialists. The opportunity of being insured, however, should not stop companies from building their own system of protection and developing their cyber resilience. After all, having an advanced level of security will lower the price of the premium, and specific security measures will even be required for cyber insurance to be arranged at all.
Questions you might be asked when applying for cyber insurance
- Can you give us general information about your company, such as your geographical area of function, annual turnover, and how much personal data you manage?
- Do you utilize multi-factor authentication (MFA), Identity and Access Management (IAM), and Privileged Access Management (PAM) controls to lower your risks?
- Do you patch and upgrade regularly?
- Are your networks segmented?
- Do you have an inventory of your software and hardware assets?
- Do you have endpoint protection software on all your computers?
- Do you use firewall?
- Do you regularly back up your data on an external media / protected cloud service?
- Are your mobile devices secured – for instance, via data encryption?
- Are your employees regularly informed about possible cyber risks?
- Do you have a functional incident response plan?
Source: Federation of European Risk Management Associations, Preparing for cyber insurance
Cyber insurance can help you – but not always
Insurance companies like to promote cyber insurance as a product that is ultimately indispensable for companies of all sizes, and even for individuals. It should cover both first-party risks of cyberattacks, meaning the loss or damage to your own data, and third-party risks, which include the liability to clients or government and regulatory entities. Supposedly, cyber insurance may help you with the costs of breach notification, forensics, remediation, data restoration, and also regulatory fines and fees, or lawsuits and claims brought by the affected customers. When a business is struck by a cyberattack, one of the greatest financial burdens resides in the momentary business interruption before danger has been successfully handled. Cyber insurance may also be of help there, offering financial assistance as well as specialists that can attempt to combat the attack. Still, one of the more problematic aspects of cyber insurance is paying cybercriminals when faced with successful a ransomware attack. Paying ransom is unrecommended on both practical and ethical grounds.
Why shouldn’t you pay ransom? Practically speaking.
- The decrypting tool you might be offered may never be delivered, it may be faulty, or it may even contain additional malware.
- The encryption process could have corrupted some of the data and thus you may not be able to recover it even after paying the ransom.
- The money you pay validates the crime and further finances criminal activity of the attackers.
- Paying ransom may even be illegal – for instance, when the cybercriminals have ties to terrorist groups, or when they are on sanctions lists.
- Paying ransom may also encourage cybercriminals to attack you repeatedly.
There are several potential issues the insurance might not cover. These include instances in which an employee or a contractor loses sensitive unencrypted data, other infrastructure failures that are not caused by a purposeful cyberattack, loss of data in the care of outside parties (such as some cloud services or external vendors), or loss of data from mobile devices (including tablets and laptops). Also, the insurance may not cover notifying affected customers, or the restoration of data that was damaged but not stolen. Therefore, the main entity that holds the tools capable of protecting your company remains you.
Digital resilience: How can you protect yourself?
- Be aware of your assets
Knowing the possible openings – threat vectors – for cybercriminals is one of the first steps toward an effective security system. You should definitely make an inventory of your internet-facing assets so that you can appropriately protect them. An identical rule applies to “ransomable” assets, which include IoT devices, SOHO routers, robots, control systems, and autonomous systems. If you´d like to learn more about how to measure the digital risk exposure of your business, see this article.
- Use RDPs wisely
Remote desktop protocol (RDP) can serve as a gateway to cybercriminals when used without specific security measures. According to Infosecurity Magazine, attacks against RDP between the first and the last quarter of 2020 surged by 768%, making it the most common delivery mechanism for ransomware in that year. Learn how to lower the chances of a successful RDP attack on your company here.
- Use multi-factor authentication (MFA)
In addition to strong passwords, using multi-factor authentication can strengthen the protection of your company. You should, however, opt for an MFA solution that is not SMS-based, as hackers have ways of overpowering this type of protection.
- Apart from network-attached storage (NAS), have an off-site storage backup
Your company should strive for a comprehensive backup strategy that employs not only on-site, but also off-site storage. If you want to read more on data backups and recovery, see this article.
- Patching and updates
Regular patching can help you with many risks related to various types of cyberattacks. Specific patches can improve the safety of your RDP or the aforementioned “ransomable” assets. Additionally, patching and updates count among the measures you can take to help prevent some of the most far-reaching cyberattacks, i.e., supply chain attacks.
- Make sure employees know where to report any suspicious activity
Suspicious emails or unknown alerts may not signify an immediate presence of danger, yet paying attention to these unusual situations can help you prevent potential upcoming cyberattacks. All employees should be educated on how to proceed in these situations and whom to contact. They should not be afraid to make a report. Fear among employees often originates in their belief that they are to blame for the attack, or in their attempts to avoid evoking unnecessary panic. Let them know that a quick reaction is encouraged, since it may stop a possible attack from happening.
- Have a strategy for what to do when an attack occurs
Even though you might have thorough protection, cybercriminals may still find ways to get to you. For that reason, you should prepare a response and recovery plan and make all the potential participants aware of the individual steps to take when reacting to cybercriminal activity. The plan should include alerting designated personnel, legal counsel, law enforcement, and vendors who might be able to help you, isolating and analyzing the machines affected by the attack, or even preparing a PR holding statement. Having a plan prepared is still not enough – your response strategy should also be properly tested. This might sound obvious, but according to AGCS, less than 40% of companies test their business continuity plans.
In conclusion, even though some companies may find cyber insurance desirable – including small and medium businesses (SMBs), which often need financial help when faced with an attack, or businesses relying heavily on confidentiality, such as healthcare companies or law offices – to protect a business effectively one should never overlook the necessity of digital resilience. Continuous work on increasing your own security protection can be demanding, but it pays off in the long run. As noted by Scott Sayce from AGCS, “The role of insurance has always been to ensure good risk management and loss prevention. Good cyber maturity and good cyber insurance go hand-in-hand. We buy insurance for our home, but this does not mean we leave the front door unlocked, and the same should be said for cyber security.”




