For cybercriminals, unpatched vulnerabilities open doors into your company’s network. One flaw in particular has led to millions of attacks in the past year, still afflicting many systems, often without IT admins being aware. Get to know Log4Shell, a vulnerability in Log4j, a popular open-source logging library, and keep your business safe from it.
The history of Log4Shell dates back to December 2021, when information about this zero-day vulnerability became breaking news. It received the highest rating in the Common Vulnerability Scoring System (CVSS) of 10/10, suggesting that this newbie in the digital cybersecurity landscape would be major trouble.
The vulnerability started to be used by digital thieves and various entities within hours, including by ransomware gangs and Advanced Persistent Threat (APT) groups. “Since the vulnerability affected a popular open-source library, it was easily found on numerous systems, often without companies being aware. The fact that this logging library is often an integral part of other software sometimes makes it difficult to find and fix. Log4Shell can be hidden deep down in your systems,” says Ondrej Kubovic, ESET Security Awareness Specialist.
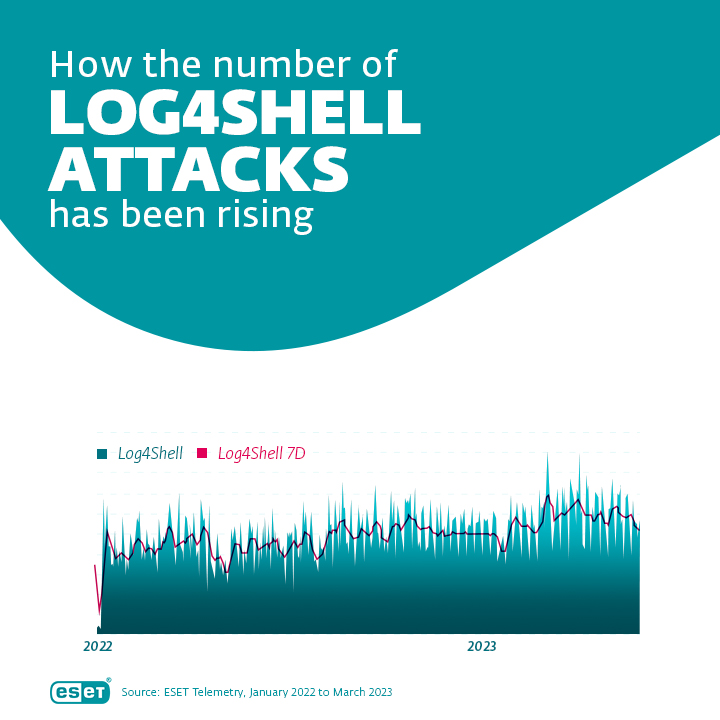
While the “gold rush moment” has passed, Log4Shell still affects many systems and has been declared endemic. In some repositories, vulnerable versions of the library are still available, which means new systems riddled with Log4Shell are still popping up on the internet. “The vulnerability often hides in outdated systems that can be difficult to patch. In some cases, the IT admin or developer might not be aware that Log4j has been used at all,” warns Ondrej Kubovic. At the same time, the number of systems being attacked via Log4Shell has increased recently – according to ESET telemetry, the number of attacks has been growing by an average of 12%.
Even though the vulnerability became public long ago, it still poses a risk. How do you prevent it from making your systems easy to breach? Run a detailed analysis of your IT infrastructure to check for forgotten or hidden Log4j instances that need patching. Also, look for anomalies that could suggest Log4Shell was, or still is, being exploited to access your company’s network.
If you plan on using the library, make sure you install a new version with the flaw fixed. If you can’t update the library or use a fixed version, monitor vulnerable deployments more closely, or preferably, take them offline. Finally, use a reliable digital security solution to mitigate exploitation attempts against your systems, but ultimately, plan to update the library to prevent any possibility of exploitation.
|
Digital threats differ around the world
In some countries, threats that no longer, or only rarely, appear in other parts of the world persist. For example, in developing countries, the WannaCry ransomware that took the world by storm in 2017 is still spreading via an exploit developed by the US National Security Agency (NSA), known as EternalBlue. The general notion is that this malware is no longer a serious threat, but it still impacts certain countries.
Looking for reliable digital security software that can help you defend against exploits? Check out what ESET’s got to offer. |




