Developed in the late 1980s, a firewall was one of the first security measures protecting internet users. Today, the latest next generation firewalls (NGFW) are useful for keeping your company safe online when combined with other systems. But how, exactly, do they work?
Like the fireproof wall in buildings, designed to keep a potential fire from spreading further, a firewall in computing is a security feature. It stands between you and the manifold threats coming from the internet, or even your own network when it is infiltrated by a hacker.
How does that work in practice? For example: when your browser sends a request to visit a potentially harmful website, a firewall can block you from doing so. Or, should there be an infected endpoint trying to spread malicious code, a firewall can serve as a security gateway, and stop someone from accessing the OS and your network.
It is imperative, though, that you run a correctly configured firewall, use it properly, and react when you see important notifications about possible threats. Otherwise, you can be exposing your organization to an unnecessary risk of having its security compromised.
When the American retail corporation Target was hit by a cyberattack in 2013, its security team had ignored an alert about a generic malware threat from their defense system before the attack. They had also turned off the function to automatically delete malicious software. A different approach and a well-configured firewall could have minimized the damage, or even prevented the breach entirely.
A useful tool to segment your network
While it was originally designed to secure single network perimeters, the role of the firewall is now changing. With companies and organizations increasingly using cloud-based solutions, and many employees working remotely, an attack can come from anywhere.
What hasn’t changed is the necessity for general cybersecurity. Any business needs the capability to inspect both inbound and outbound traffic for signs of suspicious activity, and be able to implement its own rules and restrictions.
Only now, firewalls need to be equipped for protecting more virtual landscapes. Many organizations are therefore investing in an NGFW hosted in the cloud or other “virtual firewalls.” Their admins need to be able to micro-segment the network as the cloud landscapes constantly change – something firewalls enable them to do. Eventually, they can use their micro-segmentation abilities to lay the groundwork for building their networks on the principles of zero trust and least privilege.

Other benefits of using a firewall
Apart from preventing unauthorized remote access and protecting your business from malicious code, a next-generation firewall brings your company additional benefits. Firewalls can protect your organization against zero-day threats, which are yet-to-be-documented exploits that may be targeting new kinds of software vulnerabilities. You can also choose to take advantage of other non-security features of firewalls: measuring or limiting the network bandwidth or restricting access to unsuitable or unapproved websites.
Some firewalls also provide the service of a virtual private network (VPN) for increased security. With the VPN, even when your employees work remotely, their connection is encrypted, which makes it harder for anyone to intercept the traffic. For businesses, we recommend using a hardware-based firewall to keep all unwanted traffic out of your network. It will also enable you to control outgoing traffic from your computers.
Keep in mind that firewalls alone will not provide your business with sufficient protection, as they should be only a part of your cybersecurity strategy. They also need to be properly managed and monitored, correctly set up, and regularly updated. But once you manage all that, you’re getting a highly flexible set of gateways that will help your admins monitor your network and increase your safety online, whether you’re using the cloud, or you have a team of employees working from home.
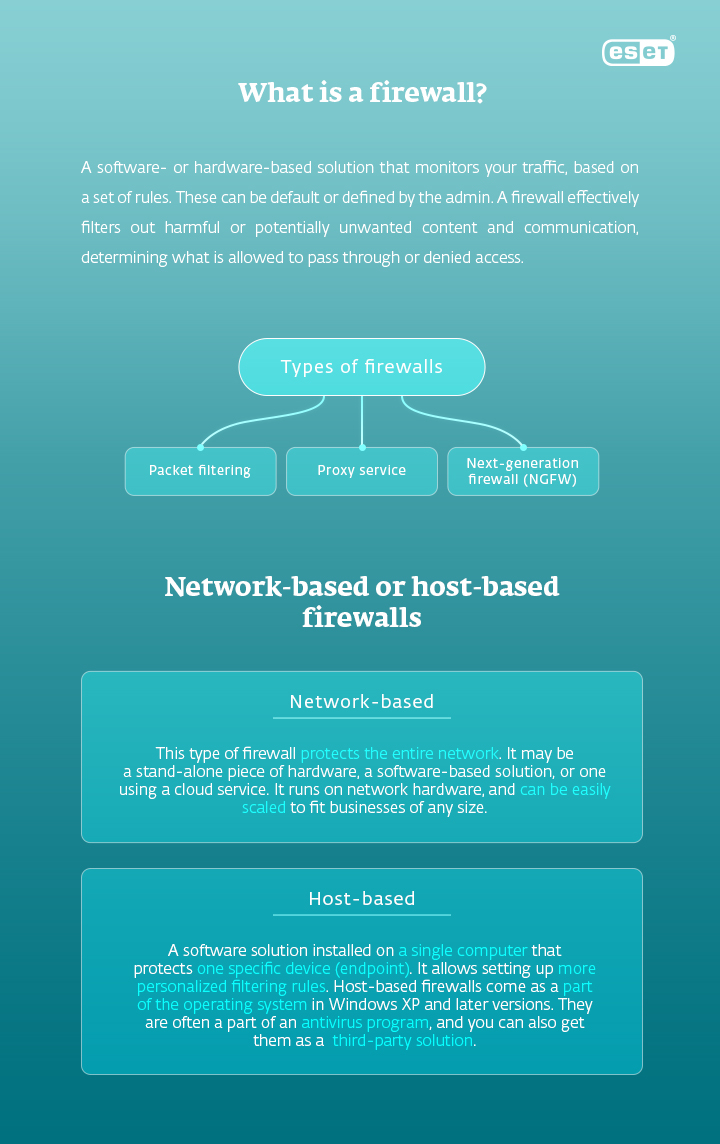
Types of firewalls
Packet filtering
Packets represent the smallest amount of data that can travel through the network. Packet filtering is a firewall technique that monitors outgoing and incoming packets of data, based on the source and destination internet protocol (IP) addresses, protocols, and ports.
Packet filtering firewalls fall into two categories: stateful and stateless. Stateless firewalls examine each packet individually – which makes them mostly unable to distinguish application-level traffic types (HTTP, HTTPS, FTP, etc.). Stateful (dynamic) firewalls, now considered the “traditional” type, evaluate filter packets, based on a larger context, as they also remember information about other packets from the same connection, as well as previously passed packets.
Proxy service
Traffic flows through the proxy server on its way to the requested address on the internet. It then comes back through the same proxy server, which forwards it to you. Proxy service also filters the traffic and controls requests from the client to keep the network secure and free of malware and unauthorized access.
Next-generation firewall (NGFW)
The latest firewalls, known as “next-generation,” combine the previous approaches with additional security systems. They may match the filtered content against a detection database, examine applications, use built-in virtual private networks (VPN), intrusion prevention and detection systems (IPS/IDS), web-filtering, or identity management.

