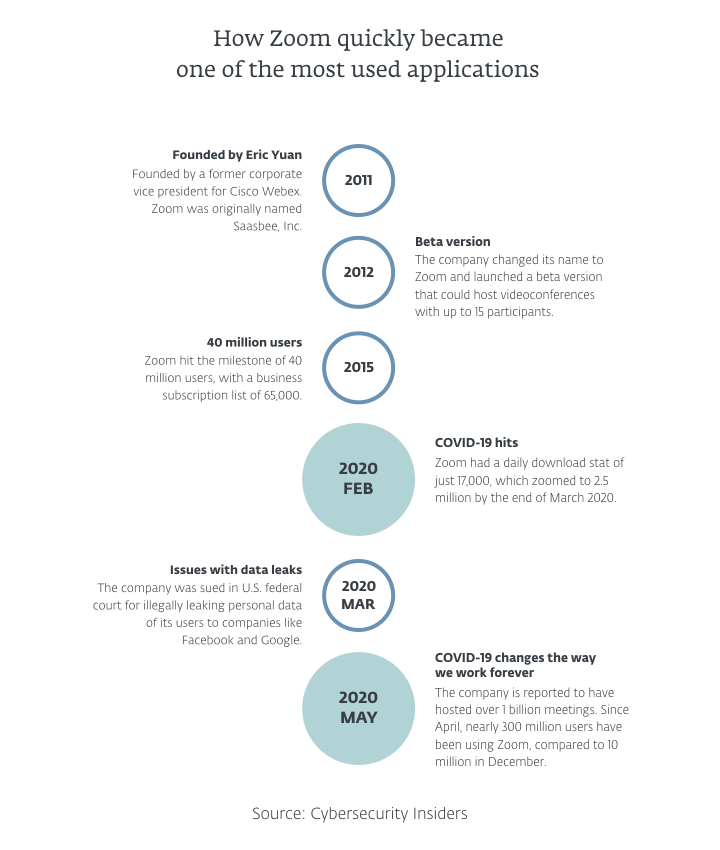
The COVID-19 lockdowns forced millions of people to work from home. With skyrocketing numbers of users, video meeting programs like Zoom almost immediately became the target of hackers.
Since the rapid changes brought on by COVID-19 related regulations, many companies have had to move their activities to the online environment – and the vast majority of them did it in record time.
However, not all of them managed to advise their employees on new cybersecurity threats related to remote work. Or they did it – ironically – while using an online videoconferencing platform.
When not properly secured, video meetings can turn into a problem. According to IFSEC, the growing demand for videoconferencing tools such as Microsoft Teams and Zoom has led to a number of privacy issues, with concerns regarding end-to-end encryption.
Justin Brookman, director of consumer privacy and technology policy at Consumer Reports magazine, emphasized how Zoom in particular has failed in terms of videoconferencing security. The FBI is now investigating several cases where hackers broke into Zoom videoconferences and threatened participants with racist, homophobic or anti-Semitic messages.
How did the hackers break into the videoconferences? By simply generating and guessing the URLs you need to join the video chats. According to Brookman, Zoom did not have to deal with so many security threats before, but by the time tens of millions of people started using the application, it had become an attractive target for uninvited guests.
The problem of annoying, and sometimes threatening, interruptions in video calls has quickly become a global phenomenon. In France, Germany and the United States, similar events have been reported and have raised concerns about the security systems of other videoconferencing platforms.
Since the so-called Zoom-bombing, researchers have found that Microsoft Teams is also vulnerable to cyberattacks. BBC wrote that attacks could be initiated in Microsoft Teams via funny GIF images. All a user had to do was view the GIF to allow an attacker to scrape data from their account. This method involves using a compromised subdomain to steal security tokens when a user loads an image. Microsoft has since patched the security hole, but researchers have warned that in the future, a similar attack could be replicated on other platforms.
On the other hand, the vulnerability of videoconferencing is also caused – once again – by users themselves. This includes the prime minister of the United Kingdom, Boris Johnson, who tweeted a picture of a virtual cabinet meeting but did not remove the meeting ID number, all during the “first-ever” digital cabinet meeting. This could potentially allow anyone to join the conversation. Nevertheless, the UK’s National Cyber Security Centre stated that if meetings are not highly classified, they can take place this way.
The key takeaway for businesses: COVID-19 and the subsequent shift toward digitalization have clearly shown the importance of strong endpoint protection and sophisticated employee training.

